
Commercial drone programmes in the UK are being accelerated due to the restrictions enforced by the Coronavirus lockdown. From medical PPE drops from mainland UK to the Isle of Wight. To the delivery of essential medicines on doorsteps in Northern Ireland. These expedited trials are the early indicators of what could be possible on-mass commercially. However, when innovations move to fast and ahead of legislation the risks and potential for misuse increases fast with them.
At the same time drones have been proven many times to be highly effective when used for malicious purposes. From delivering drugs to prisons to stopping flights from taking off and, even rendering international airport runways at a standstill for days as happened at Gatwick airport in December 2018.
Innovative drone programs, and ongoing malicious use means that commercial drones will become both attractive targets both in terms of their payloads, and the drones themselves (which are likely to have ever improving capabilities).
This raises the question of ‘what is the future of commercial drone security?’
The Threat Model
First, we need to look at some of the potential threats and who the would-be attackers are. Below is a high-level attack tree outlining possible steps attackers could take to compromise a drone.
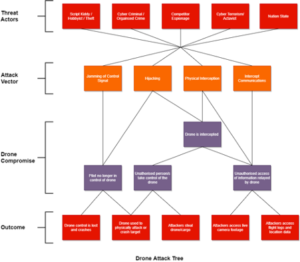
Hijacking control communications could allow an attacker to take unauthorised control of the drone
Another well documented incident happened in 2011 when an American Lockheed Martin RQ-170 (UAV) was captured by Iranian forces near the city of Kashmar in north eastern Iran purportedly brought down by the Iranian cyberwarfare unit. The Iranians then reverse engineered the drone to build copycat drones one of which was shot down and captured by the Israelis in 2018.
If this can happen to military organisations where security is of the highest level, then the implications for commercial ventures cannot be ignored.
Attacks on communications such as those used to control drones are also a valid target where compromise could result in a catastrophic outcome. By jamming the communications, the drone could lose control and crash. Hijacking control communications could allow an attacker to take unauthorised control of the drone perhaps crashing it into a target, stealing it or its cargo, or using it to cause disruption.
Location communications such as GPS are also a consideration. Imagine if an attacker could manipulate GPS data to send a delivery drone to the wrong location.
This model primarily considers attacks on the control and communications of drones, but we should also consider the risk posed by supply chain attacks or attacks targeting operating systems or software. Many long-range drones are controlled remotely from base stations by human operators. It might prove difficult to break into the buildings and take over the drones, but if attackers target the control software and remote hack into the systems then they could bypass the human operators.
We can look at car manufacturers that issue vehicle software updates over the air to see the potential of this as an attack vector. In 2017 a Chinese white hat hacker group, managed to remotely hack the Tesla Model S through a malicious Wi-Fi hotspot and take over various controls including the braking system.
It is also likely that commercial drone enterprises will rely on similar systems to manage a fleet of drones from control bases. As most hobbyist drones use inexpensive IOT control boards and off the shelf software that is notoriously insecure. It is likely many commercial offerings will use similar software and components with inherent vulnerabilities to lower costs which if not thoroughly tested or secured will lead to security weaknesses.
With state and terrorist cyber-attacks on essential infrastructure well documented. It is not a far leap to see the attraction to threat actors of taking over a flock of drones for miscreant purposes.
This leads to two questions:
- How do we ensure proper security testing and auditing of drone technology in the commercial space?
- How do you measure and insure the cyber risk of the commercial drone market without such testing?
In regards to the first question, the CAA has regulations contained within the Air Navigation Order 2016 (ANO 2016) with specific additional steps that must be taken if a drone is being flown for commercial operations. This is good but simply puts the onus onto the company operating the drone to comply with a set of regulations in relation to the flying and operating of the drones, and does not tackle the underlying subject of security testing and resilience against attacks targeting commercial drones or their reliant infrastructure.
What is needed is a proper set of security standards that all commercial drone operators adhere to pertaining to stringent security testing and threat mitigation. Until then the space will be a wild west of varying security standards and safety with potentially life-threatening outcomes.
For question number 2, the answer is that without proper security testing and auditing you cannot. Without that there is no way to reliably measure or mitigate the risk. The cyber insurance markets already grapple with technology moving at ever increasing pace with new threats and attack vectors uncovered on an almost daily basis, drone technologies are only going to complicate matters.
For now it is the responsibility of each commercial drone enterprise to ensure full and proper security testing and risk assessment of the entire pipeline and all technologies that are in operation. From the components used to build the drones, control systems, software, and operating systems to the procedures used to fly and manage the fleet. Performing these security tests is not only is good practice but it makes long term financial sense given in the event of a drone related incident who would be held liable.
If you are operating in the commercial drone space and would like to discuss security testing or how our services would help your organisation, then please visit www.occamsec.com or contact us at: info@occamsec.com

