
While Sim Swapping has been a threat for nearly 10 years, it has gained in popularity mostly due to an emerging hacking group called Lapsus who have successfully targeted Microsoft, Uber, Samsung, T-Mobile, Nvidia, Ubisoft, Rockstar Games, as well as Brazil’s Ministry of Health all since December, 2021. Another group that has had success using Sim Swapping is 0ktapus, who have successfully attacked Okta, Twilio and Mailchimp all in the same operation in August, 2022.
For the nonprofessionals, Sim Swapping occurs when threat actors obtain key details about the life of the target, are able to correctly answer security questions, impersonate the target, and convince the target’s mobile carrier to reassign a new virtual Sim card to the device which the threat actor now controls.
Sim Swapping targets a weakness in Two Factor Authentication (2FA) whereby the second factor, is typically an SMS text message. Where does the weakness lie? Let’s examine some common authentication techniques:
- Email and Password login – received either on computer and/or handheld device
- One Time Password (OTP) code sent to device via text or call
- New device authentication via email – received either on computer and/or handheld device
The problem with these login processes is everything listed above is obtainable when a threat actor executes a Sim Swap and all of the target’s text messages are routed to the threat actor who can then authenticate themselves as the target. Therefore, when the threat actor has access to the first account, they can reset the password of any account that authenticates using SMS 2FA. This makes the common 2FA (login + SMS) or 3FA (login, SMS + OTP to phone) a less secure option for authentication.
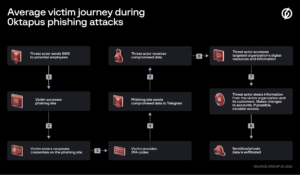
Figure 1 – A visual representation of how attackers can Sim Swap via phishing.
Source: Group-IB, 2022
How does a threat actor perform a Sim Swap?
Stealing devices to perform Sim changes. A threat actor may target a retail business, and simply enter a store and steal a device from an employee’s hand to gain access to an allow-listed system for a limited amount of time (typically 1-6 hours ) until the device is block-listed from the network. During this short window of time, they have access to accounts to Sim Swap as if they were an actual employee.
Gaining access to corporate systems via social engineering of login credentials. For example, a threat actor could gain access to Citrix (or other remote access) systems and Social Engineer an unsuspecting employee. Social Engineering can also occur through a customer service phone call, or live chat whereby the threat actor convinces a mobile provider to authenticate the stolen Sim via OTP through email to the device they now control.
Bribe low paid staff at an Internet Service Provider, Mobile Telecom, or really any company with targeted accounts to perform Sim Swaps while promising them future financial bonuses.
How do you mitigate a Sim Swap, if you are responsible for a company’s device policies?
Enforce mandatory 3FA with hard tokens and restrict or eliminate access of junior level employees to making changes to accounts.
Prevent the use of email or SMS as an authentication tool.
Enforce password changes monthly.
Disallow outbound connections and non-allow-listed IPs from connecting into Citrix or other remote access instances.
Enforce a second approval for legitimate Sim swaps to be performed (staff and manager or supervisor must each approve, for example).
How do you mitigate a Sim Swap if you are a user?
Disallow all 2FA via SMS or phone call on personal systems.
Enforce 2FA via security key hard tokens such as Yubikeys or Titan keys (not an endorsement of either product).
Ensure passwords are strong (12 characters), different from the last password, with no correlation to any personal info (pet’s name, kid’s name, partner’s name, anything that can be gleaned from social media channels), stored safely in an offline password manager such as KeePass or an online password manager like LastPass (not an endorsement of either product).
Never store passwords in web browsers autofill or on Google accounts as they are frequently targeted and vulnerable.
When facing security questions as a method of resetting your password / 2FA method, treat those security answers like a password and fill them with random characters and ideally saved to a password manager.
Security is harder than the frictionless dream of the average TED talk, or giant corporate product launch. These changes may cause headaches in a workspace or personal environment. Implementing some or all of these steps will improve your security posture and limit the damage caused by Sim Swap attacks. Humans will always be the weak point of any system and we cannot stop them from being socially engineered. What happens after is the cause for concern and where we can make a difference. Implementing these precautions will limit the damage Sim Swap attacks can cause.
