Summary
At OccamSec, we understand that cyber threats are constantly evolving and becoming increasingly sophisticated. To help organizations stay ahead of these threats, we offer a comprehensive Threat Hunting service. Our team of experienced security professionals uses advanced techniques to proactively identify and neutralize potential threats before they can cause harm.
What is Threat Hunting?
Threat hunting is the process of proactively searching for signs of malicious activity within an organization’s networks, systems, and data. Unlike traditional security approaches that focus on detecting and responding to known threats, threat hunting looks for indicators of compromise (IOCs) that may not be immediately apparent or previously identified. This approach allows organizations to identify and neutralize potential threats before they can cause damage.
Our Threat Hunting Service
Our Threat Hunting service is designed to provide organizations with a proactive approach to cybersecurity, filling the gaps left by traditional security measures that often miss advanced, persistent threats. With the increasing sophistication of cyberattacks and the rise of new threat vectors, it’s no longer enough to rely solely on preventative measures like firewalls and antivirus software.
In fact, there are numerous real-world examples of attacks evading detection for extended periods, causing significant damage to organizations. For instance, the infamous Target data breach in 2013 went undetected for months, exposing the sensitive information of millions of customers. Similarly, the Equifax data breach in 2017 wasn’t discovered until several months after it began, leading to the theft of personal data belonging to over 140 million people.
Our Threat Hunting service addresses these challenges by actively seeking out and identifying potential threats that may have slipped through the cracks of traditional security measures. Our team uses advanced techniques, including machine learning and artificial intelligence, to gather threat intelligence from a variety of sources and analyze data within our clients’ networks, systems, and applications.
By proactively hunting for threats and assessing their risk level, we can help organizations prevent attacks before they occur and minimize the impact of any detected threats. Our Threat Hunt service includes threat intelligence gathering, data collection and analysis, threat detection, incident response, and regular reporting and documentation to ensure our clients are well-informed and equipped to maintain a strong security posture.
Case Study: Proactive Threat Hunting: Uncovering Boleto Fraud in a Complex Financial Environment
Benefits
Our Threat Hunting service provides organizations with several benefits, including:
1. Proactive Threat Detection: By proactively searching for potential threats, we help organizations identify and neutralize them before they can cause harm. This approach reduces the risk of data breaches, system downtime, and reputational damage.
2. Improved Security Posture: Our team provides detailed recommendations for improving our clients’ security posture based on the data collected and analyzed. This includes implementing new security controls, updating policies and procedures, and providing training to staff members.
3. Regulatory Compliance: Our Threat Hunt service can help organizations meet regulatory requirements related to cybersecurity and data privacy. We provide detailed documentation and reporting to demonstrate compliance with relevant laws and regulations.
4. Cost Savings: By identifying potential threats early, we help organizations avoid the costs associated with data breaches, system downtime, and incident response efforts. This can result in significant cost savings over time.
5. Peace of Mind: Our Threat Hunt service provides organizations with peace of mind knowing that their networks, systems, and data are being monitored and protected by experienced security professionals.
Process
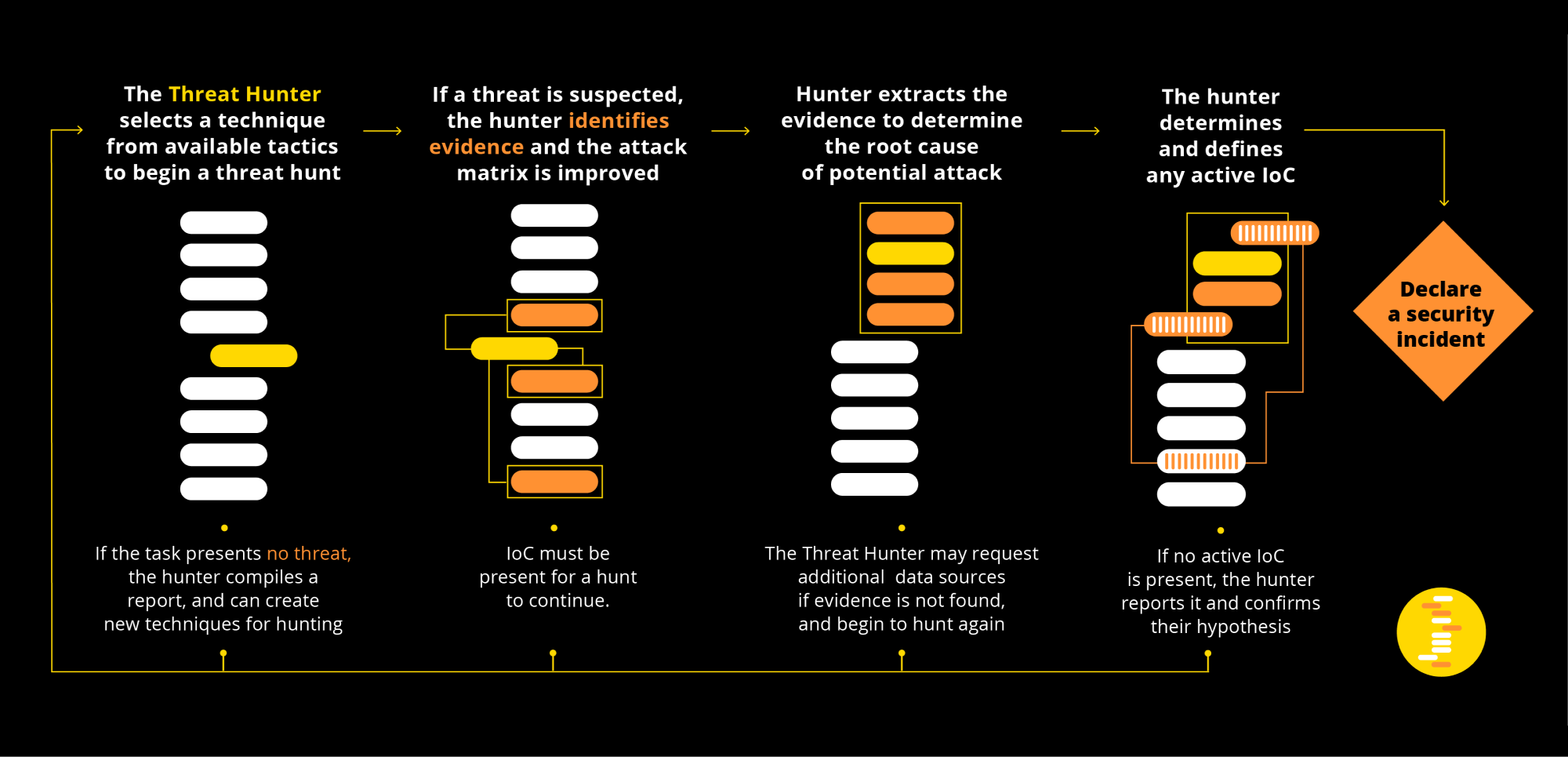
Our Threat Hunt service follows a comprehensive and iterative process to identify and neutralize potential threats before they can cause harm. Our team uses advanced techniques, including machine learning and artificial intelligence, to analyze data from various sources within our clients’ networks, systems, and applications. Here are the specific steps involved in our Threat Hunt service:
1. Threat Intelligence Gathering: We gather threat intelligence from a variety of sources, including open-source intelligence (OSINT), proprietary databases, and industry partners. This information is used to identify potential threats and assess their risk level. Our team uses advanced techniques, such as natural language processing and machine learning algorithms, to analyze this data and identify emerging trends and patterns. We also work closely with our clients to understand their specific threat landscape and ensure that we are focused on the most relevant risks.
2. Data Collection and Analysis: We collect data from various sources within our clients’ networks, systems, and applications, such as log files, network traffic data, and user behavior analytics. Our team uses advanced techniques, including machine learning and artificial intelligence, to analyze this data for indicators of compromise (IOCs) and other signs of potential threats. We use a variety of methods, such as statistical analysis, anomaly detection, and behavioral analysis, to identify suspicious patterns and behaviors that may indicate the presence of a threat.
3. Hypothesis Development: Based on the data collected and analyzed in the first two steps, our Threat Hunt team develops a hypothesis about potential threats or vulnerabilities that may exist within our clients’ systems or networks. This hypothesis is used to guide further analysis and investigation.
4. Evidence Collection and Analysis: Our Threat Hunt team collects and analyzes evidence to test the hypothesis developed in the previous step. We use advanced techniques, such as threat modeling and attack simulation, to understand how potential threats may exploit vulnerabilities in our clients’ systems and networks. We also work closely with our clients to gather additional information that may be relevant to the investigation.
5. Attack Matrix Improvement: As more analysis is done and evidence is collected, our Threat Hunt team refines the attack matrix used to identify potential threats. This includes updating the tactics, techniques, and procedures (TTPs) used by threat actors and improving the accuracy of our predictive models.
6. Detection: During this phase, our Threat Hunt team seeks to determine the root cause of any identified attacks or vulnerabilities. We use advanced techniques, such as digital forensics and incident response (DFIR), to investigate incidents and gather evidence that can be used for prosecution or other legal purposes.
7. IOC Definition: Our Threat Hunt team identifies and defines any active indicators of compromise (IOCs) that may be present in our clients’ systems or networks. This includes developing signatures and alerts that can be used to detect and prevent future attacks.
8. Incident Response: In the event that a threat is detected, our team works closely with our clients to respond quickly and effectively. This includes containment, eradication, and recovery efforts, as well as post-incident analysis to identify root causes and prevent future attacks. Our team uses advanced techniques, such as DFIR, to investigate incidents and gather evidence that can be used for prosecution or other legal purposes.
9. Reporting and Documentation: We provide regular reporting and documentation to our clients, including detailed threat intelligence reports, incident response summaries, and recommendations for improving their security posture. Our team also provides training and support to help our clients implement these recommendations effectively. We use a variety of methods, such as dashboards and visualizations, to make this information easily accessible and understandable to non-technical stakeholders.
10. Continuous Improvement: Our Threat Hunt service is designed to be iterative, with regular assessments of our clients’ security posture and adjustments made as needed. We work closely with our clients to ensure that their defenses are always up-to-date and effective against the latest threats. Our team uses advanced techniques, such as threat hunting and purple teaming, to proactively identify potential vulnerabilities and weaknesses in our clients’ systems and networks.