Introduction
This month’s Patch Tuesday sees 79 fixes for September. Of the issues found, 19 are of a high severity and likelihood of exploitation in the future. In the wild, 4 have been actively exploited by threat actors (with one having been exploited since 2018). The class of vulnerabilities this month are continuing trends from last month including issues that bypass Microsoft SmartScreen and privilege elevation being most prominent.
Key Details
- As social engineering such as phishing, vishing, and so on are prime vectors for initial exploitation, we are continuing to see bypass and spoofing related vulnerabilities month to month. Both MSHTML and MotW remain prominent targets.
- The issues exploited in the wild are also higher than average, while not as high as last month, it is elevated this month from the average of 2-3 in-the-wild exploitation.
- Privilege escalation bugs are what are also seen on a monthly basis being exploited, combined with initial social engineering vectors and related issues, turns this into a one, two punch in regards to most threat actor tactics at the beginning of their attack chain.
Analyst Comments and Recommendations
A lesser cadre of issues have emerged this month (especially in comparison to previous Patch Tuesday cycles), however the number of exploited issues in the wild this month is slightly above the average we’ve been seeing in comparison to previous months. With the exception of last month which saw 6 vulnerabilities versus this month’s 4. However, the vulnerabilities exploited in the wild are a more predictable lot. Social engineering campaigns are typical of initial perimeter access for threat actors and the issues exploited this month represent that with MotW security bypass and other spoofing issues. Aside from elevation of privilege bugs, we see a return to form with potential new Office macro exploitation also in the mix.
This is a trend that is likely not slowing down, as humans tend to be the weakest link in the chain, it’s much easier (and quicker) for threat actors to take advantage of over manually exploiting a perimeter device and doing the leg work of proxying into an internal environment to deploy their tools. As a lot of threat actors (particularly ransomware operators) operate on a business model that they sell to affiliates, easier and faster exploitation usually pays dividends if they can exploit target organizations faster.
Given this, it’s not only recommended to shore up the primary perimeter defenses but take an approach where you assume that the wolf is not at the door but already inside the house. Ensure users are not overly privileged within the network and take special care to train staff to not accept or click executables (or any file) from an unfamiliar sender. As the threat landscape is moving more towards targeting users, employee workstations, devices, and so on, ensure thorough auditing and regular patching schedules for employee devices.
EXPLOITED In the Wild
This section details the vulnerabilities that have been known to be abused in the wild. These issues should be taken care to be remediated within the environment as known exploitation has taken place and organizations in targeted sectors should take especial care in ensuring these items are mitigated within their environment as soon as possible.
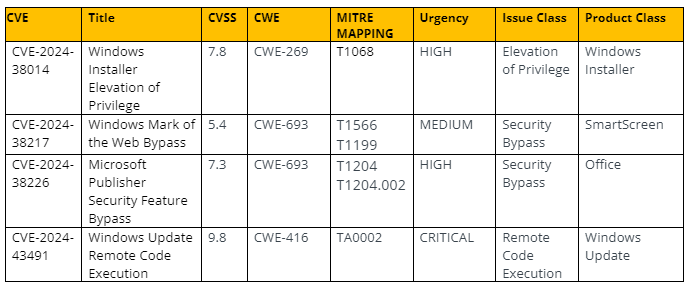
CVE-2024-38014 – WindoWS installer Elevation of Privilege
Details are scarce for this issue affecting Windows Installer, but successful exploitation would result in local SYSTEM level privileges on the victim host. As threat actors generally take advantage of file manipulations for Microsoft features and services , it would not be a large assumption to assume that the likely vector is a malicious app installer file. However, this is unverified until more details of this issue come out. This affects versions of Windows 10,11, and Server 2008, 2012, 2016, 2019, 2022.
CVE-2024-38217 – Windows MArk of the Web Feature Bypass
The following issue is a Mark of the Web (MotW) feature bypass issue that is able to remove the MotW from files in order to bypass SmartScreen protection. This follows with current trends of threat actors exploiting this in order to avoid setting off SmartScreen protections that would alert and prevent users from executing unknown and potentially malicious files downloaded from the internet. Currently, there is publicly available research and Proof-of-Concept (PoC) code available for this issue. This issue affects Windows versions 10,11 and Servers 2008, 2012, 2016, 2019, 2022.
CVE-2024-38226 – Microsoft Publisher Security Feature Bypass
According to the Microsoft Vulnerability guide, this would allow bypass of Office macro policies to execute remote code. It is unknown if the threat vector would be in the form of an Office file (such as Word, Excel, and so on), however the requirements in the CVSS scoring for user interaction and local execution likely support this assumption and likely something that would be served via phishing or other social engineering vectors.
CVE-2024-43491 – Windows Update Remote Code Execution
This issue affects only an outdated version of Windows 10 (version 1507) and would result in execution of code by triggering a use-after-free vulnerability in Windows Update for this version. This is due to a rolled back update affecting only this specific version of Windows and does not affect server versions. However this does affect IoT implementations of this Windows version, which might also incorporate industrial level controls or infrastructure that would elevate the risk involved with this version. No public Proof-of-Concept code is available.
Most Likely To Be Exploited
This section details the vulnerabilities that are likely to be abused in the wild in the future, and/or have public research or PoC code available that elevates the likelihood of being taken advantage of by an advanced threat.
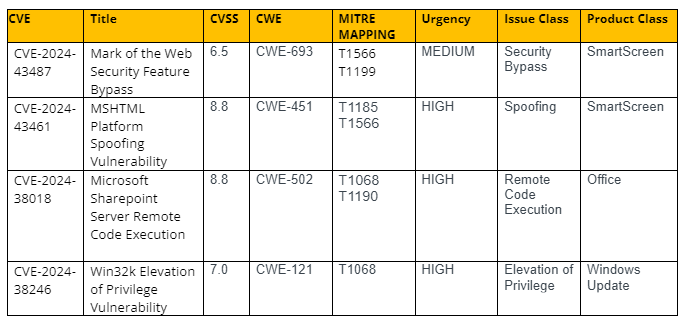
CVE-2024-43487 – Mark of the Web Security Feature Bypass
Another MotW security feature bypass vulnerability, similar to the other CVE noted above. Much like it as well, allows an attacker to bypass SmartScreen in order to execute malicious code. Given the recent tactics of threat actors using similar bugs to their advantage, it is with a fair bit of certainty that this issue will also be one abused in the wild. This affects Windows versions 10,11 and servers 2012 and 2016.
CVE-2024-43461 – MSHTML Platform Spoofing Vulnerability
An MSHTML Platform spoofing vulnerability exists affecting multiple Windows and Windows Server versions. While little details exist on this issue, some sources claim that it is a clickjacking bug. While typically, clickjacking by itself is not a high nor critical finding, however there are likely circumstances that make it easier to exploit and weaponize in social engineering campaigns targeting users for greater impact than is usual for this bug class. As this same vector has been abused in the past by threat actors to bypass security controls to get users to open malicious LNK files without SmartScreen triggering, another issue in this space has been of particular interest. This affects Windows versions 10,11 and 2008, 2012, 2019, and 2022.
CVE-2024-38018 – Microsoft SharePoint Server Remote Code Execution
This is a deserialization bug that can be exploited by an authenticated malicious actor if they hold a minimum of the Site Member permissions. This can be abused over the network and result in execution of code on the server. Given the wide adoption of SharePoint as a knowledge repository for many corporations that is made externally and internally available on networks, this is typically a “juicy” target for threat actors looking to learn the structure, processes, and/or credentials of a target organization. This affects SharePoint server 2016, 2019, and subscription versions.
CVE-2024-38246 – Win32k Elevation of Privilege Vulnerability
The issue is noted as being a stack-based overflow and requires that a race condition also needs to be won for successful exploitation of this issue. If successful, the attacker would gain the privileges of a local SYSTEM user on the vulnerable host. As a similar issue was found exploited in the wild in August, it makes sense to note this similar issue here that also has a high likelihood of being used in a threat actor attack chain. This affects Windows versions 10,11 and Server 2022.
Year to Date Trends
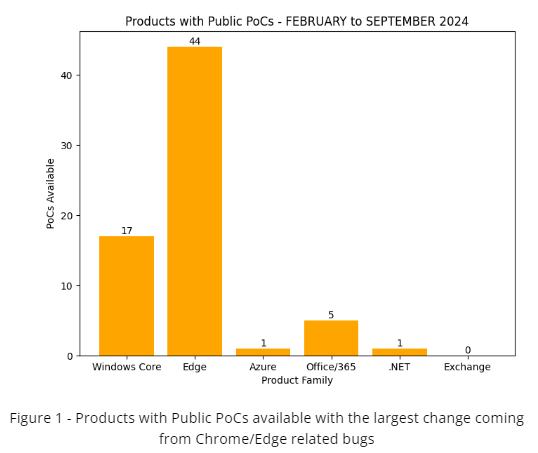
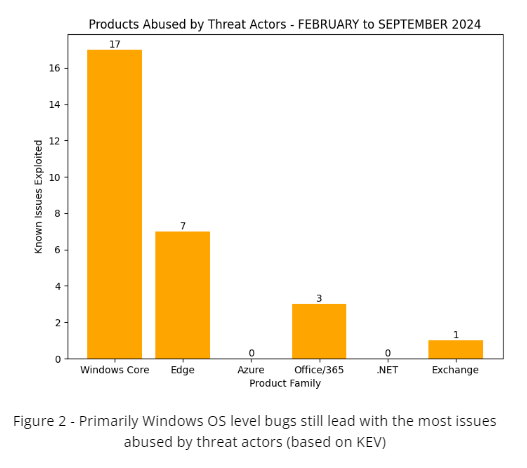
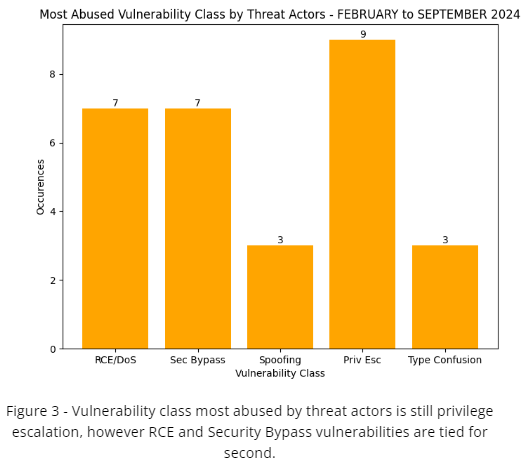
The following trends have been observed since February (first Patch Tuesday month of 2024) in regards to issues with known PoCs or known to be exploited in the wild. From February to September of 2024 there are currently 68 known publicly available PoCs or research and 28 known issues to have been abused by threat actors. A majority of the changes for PoCs are for Chrome/Edge related bugs. However, Windows OS and Security Bypass, Privilege escalation, and remote code execution related issues still remain a favorite of threat actors.
References
Microsoft Learn – Creating appinstaller files
https://learn.microsoft.com/en-us/windows/msix/app-installer/how-to-create-appinstaller-file
Elastic – Dismantling Smart App Control
https://www.elastic.co/security-labs/dismantling-smart-app-control
Vulners – CVE-2024-43461
https://vuldb.com/?id.277074
Fortiguard Blog – MSHTML Platform Spoofing (Past but similar vulnerability)
https://www.fortiguard.com/threat-signal-report/5494/windows-mshtml-platform-spoofing-vulnerability-cve-2024-38112
Microsoft Vulnerability Update Guide
https://msrc.microsoft.com/update-guide/vulnerability/
Bleeping Computer – Microsoft Fixes Windows Smart App Zero-day Exploited since 2018
Red Canary – Mark of the Web Bypass
https://redcanary.com/threat-detection-report/techniques/mark-of-the-web-bypass/
